A Vpn Policy Should Address Which Authorization Methods Are Permitted On The System
A vpn policy should address which authorization methods are permitted on the system. Authentication authorization and accounting. This VPN mode establishes a VPN connection between a. Question 14 5 5 pts A VPN policy should address which authorization methods are from ITN 263 at Tidewater Community College.
Vpn Policy Address Authorization Methods Permitted System True False Q39262894. They do not provide VPN connection or intrusion detectionprevention services. Enjoy Private Browsing with a VPN.
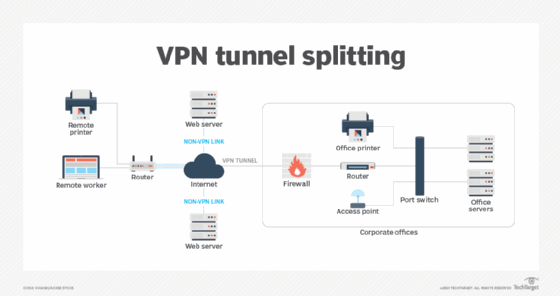
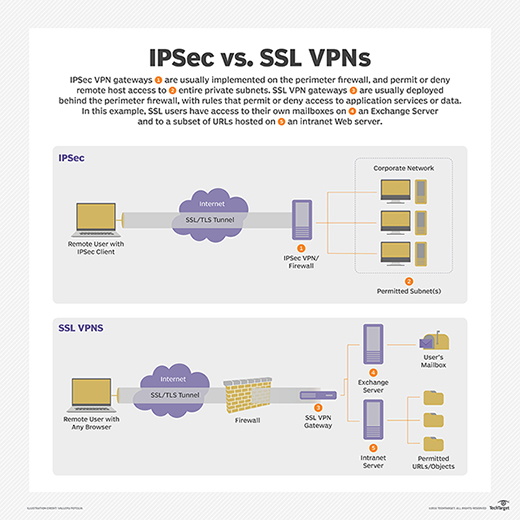
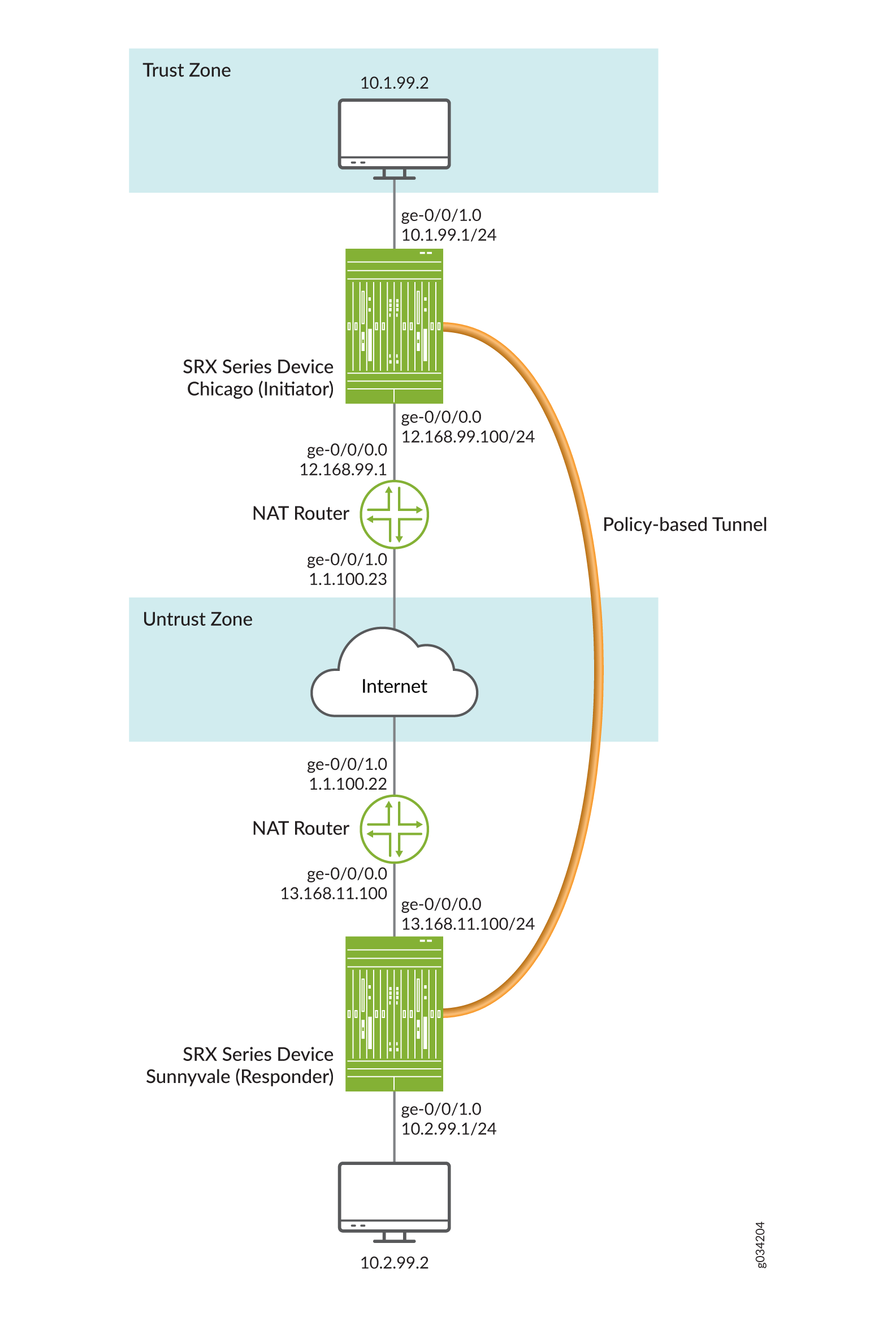
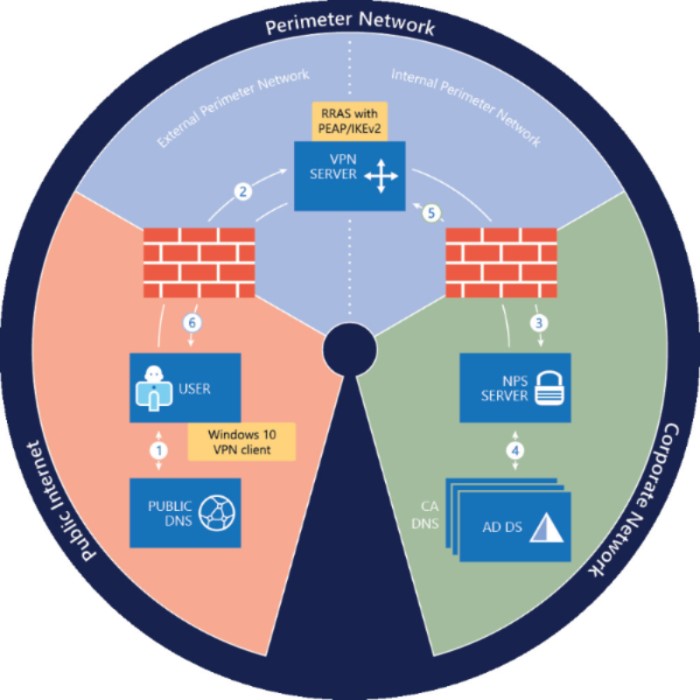
View the full answer. The corporate security policy dictates that the traffic from the remote-access VPN clients must be separated between trusted traffic that is destined for the corporate subnets and untrusted traffic destined for the public Internet. It is a software application that provides access to all users so when a user logs in the VPN contacts the RADIUS application which authenticates the user through the Mac Windows or another OS.
Ad The Best VPN Providers for Streaming Anonymity Security. Enjoy Private Browsing with a VPN. A VPN policy should address which authorization methods are permitted on the system.
Anonymity Question 8 of 44 A VPN policy should address which authorization methods are permitted on the system. Bypassing the normal authentication process. Compare e encontre sua VPN ideal.
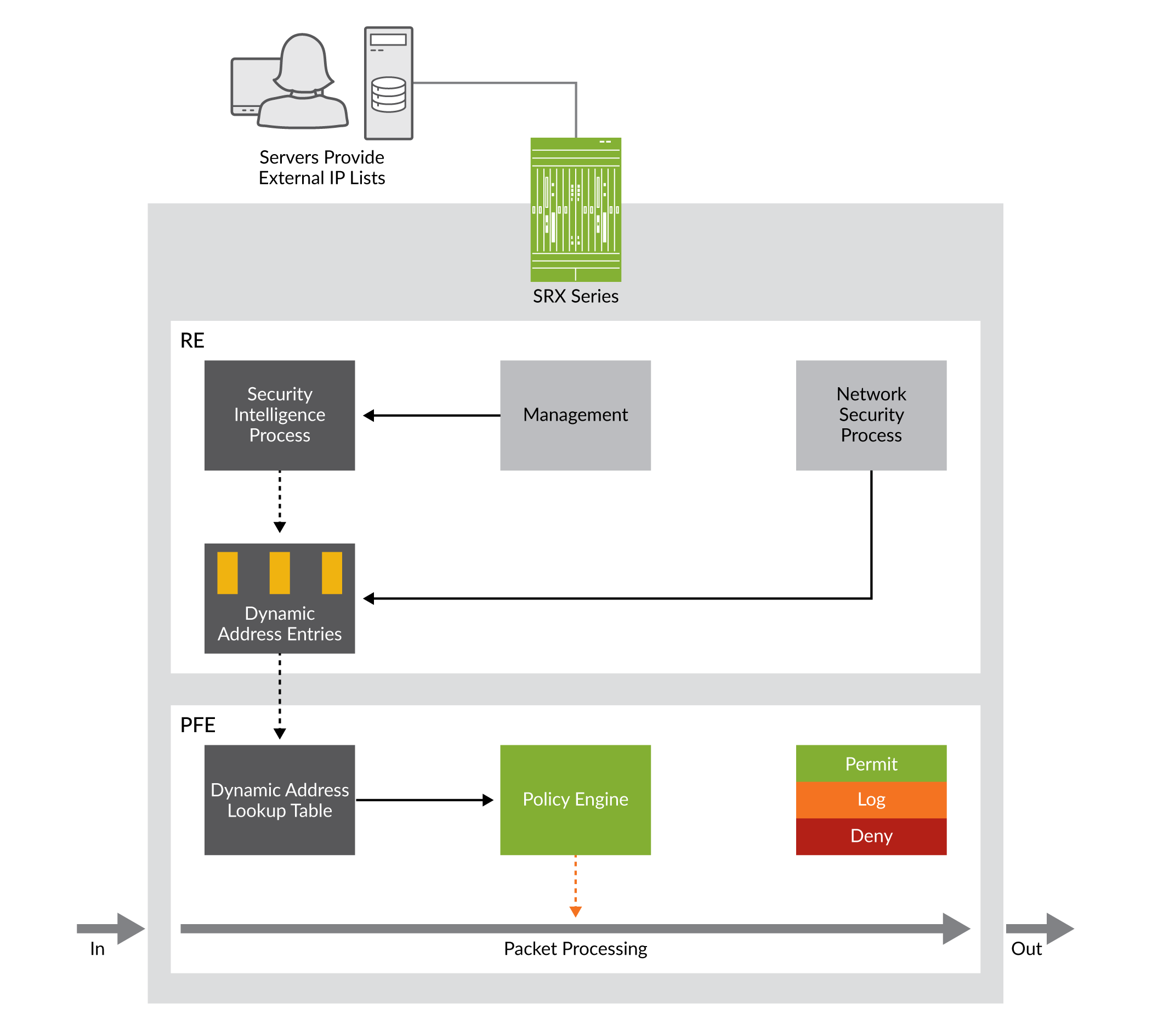
A RADIUS server can be used for central authentication when implementing a secure and effective VPN remote access policy. Access Content from Anywhere - on Any Device. They provide four important functions.
Compare Now Find Your Ideal VPN. Posture assessment evaluating an incoming device against the security policies quarantining of non-compliant systems and remediation of noncompliant devices.
They do not provide VPN connection or intrusion detectionprevention services.
Mude o seu IP. Vpn Policy Address Authorization Methods Permitted System True False Q39262894. A VPN policy should address which authorization methods are permitted on the system. Choose The Perfect One For You. Bypassing the normal authentication process. It defines things like who can use the VPN what they can use it for and what it is that keeps them from using improperly or maliciously. True False Question 14 5 out of 5 points Anonymity is the capability of a network or system user to remain known on the system. Anonymity Question 8 of 44 A VPN policy should address which authorization methods are permitted on the system. It is a software application that provides access to all users so when a user logs in the VPN contacts the RADIUS application which authenticates the user through the Mac Windows or another OS.
A VPN policy should address which authorization methods are permitted on the system. The corporate security policy dictates that the traffic from the remote-access VPN clients must be separated between trusted traffic that is destined for the corporate subnets and untrusted traffic destined for the public Internet. They provide four important functions. We Curated the 7 Best VPN Services. A RADIUS server can be used for central authentication when implementing a secure and effective VPN remote access policy. Posture assessment evaluating an incoming device against the security policies quarantining of non-compliant systems and remediation of noncompliant devices. A VPN policy should address which authorization methods are permitted on the system.























.jpeg?revision=1&size=bestfit&width=890)

Post a Comment for "A Vpn Policy Should Address Which Authorization Methods Are Permitted On The System"